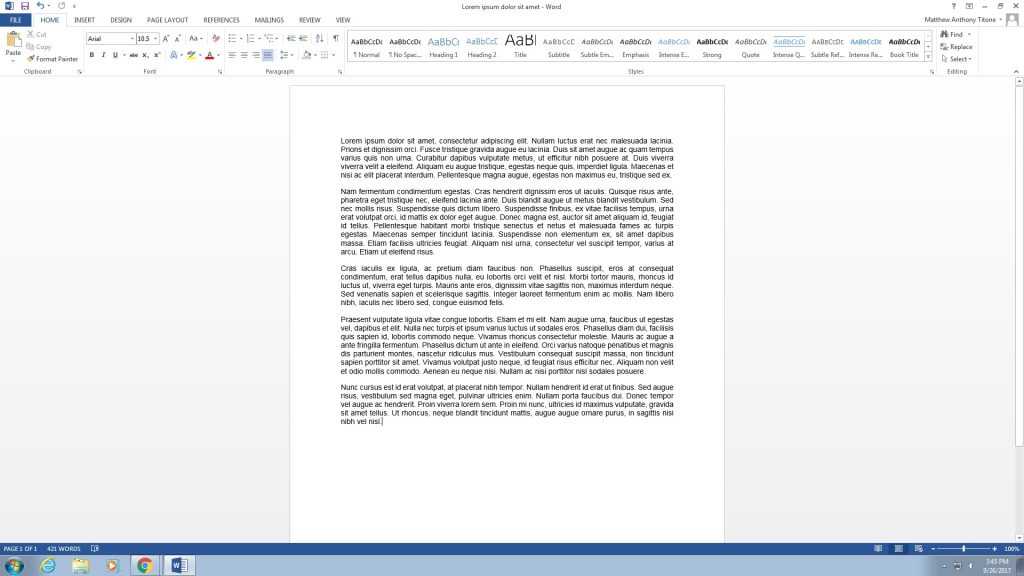
Nautical charts are channels which portray water regions instead of land locations. These fundamental ab tools describe the physical characteristics of oceans, seas, lakes, rivers and coastlines.
Nautical charts also explain underwater attributes, list water tanks, reveal navigational aids and offer a number of different details that help in navigating the sea safely.
Mariners rely on nautical charts to plot the most efficient path between harbors and browse active castles without collisions. Nautical graphs guide seafarers through dangerous passages or into distant islands from the open sea.
Since nautical graphs play a crucial role in safe navigation at sea, they hold more power than conventional maps. While maps reveal predetermined streets and paths, navigational charts make it possible for mariners to chart their own course across any waterway, sea or sea.
Nautical charts have a great deal of advice, which might appear intimidating to new boaters. However, as soon as you become knowledgeable about the fundamental characteristics of nautical charts, you may read navigational charts such as a legitimate mariner. Here are some significant climatic chart symbols and terms to understand:
- CHART SCALE
Nautical charts arrive in various scales, based on the locale of water that they pay. Charts depicting huge regions of water possess a bigger scale and also show less detail, even while graphs depicting little water regions have a bigger scale and reveal more detail.
Scale is recorded on nautical charts as a portion. The first number signifies one inch over the graph, and the second number represents the equal number of inches around the ground. By way of instance, on a nautical chart using a 1/40,000 scale, 1 inch on the graph represents 40,000 inches over the water. This is equal to approximately 0.55 nautical mph on the graph.
Nautical charts vary from quite detailed harbor graphs with scales around 1/20,000 to overall graphs depicting hundreds of kilometers of open sea with scales as little as 1/1,200,000. When choosing a navigational chart for the travel, pick a suitable scale which covers the area you intend to traverse, while providing enough detail to get you there safely.
- DEPTH MARKINGS AND CONTOUR LINES
Depth is indicated on nautical charts as amounts published on various water locations. Based upon the age and scale of this graph, depth numbers can signify feet, fathoms or meters.
The device of thickness on a nautical chart is usually listed in the upper right corner in big print. Listed below are a Couple of necessary conditions for studying nautical chart symbols for thickness:
Fathoms: While many contemporary graphs indicate depth in meters, elderly NOAA charts may use fathoms, abbreviated as FM. A fathom is equal to 6 feet. Depth dimensions in fathoms which aren’t a multiple of six are recorded using subscripts. By way of instance, the thickness signaling 45 FM signifies 4 fathoms and 5 ft, or 29 ft.
Mean Lower Low Water: The true thickness of a water place is usually greater than the thickness amount listed on a specific chart. This is because thickness numbers signify the Mean Lower Low Water Depth (MLLW) of the region. MLLW is the normal height of the lowest wave recorded every single day throughout the 19-year recording interval known as the National Tidal Datum Epoch (NTDE).
Lowest Astronomical Tide: Several nautical charts depict depths by the Lowest Astronomical Tide (LAT) rather than MLLW. LAT is the smallest wave expected to happen in a water place dependent on the NTDE. Unless you’re drifting during unusually low tide time , the true depth will almost always transcend the LAT thickness recorded.
Along with thickness numbers, nautical charts also portray depth with contour lines. Depth contour lines join areas of the identical thickness to supply a clearer image of the shape of the seabed beneath your ship. Contour lines are especially helpful when traveling near coastlines. On certain nautical maps, shoal regions are indicated with warmer shape lines or shaded regions for smoother browsing in shallow waters.
- DISTANCE MARKINGS — THE NAUTICAL MILE
The space on nautical charts is calculated in nautical miles, abbreviated as M or NM. Nautical miles are more than statute miles on property, measuring 6,706 ft. But, one nautical mile is equivalent to exactly 1 level or a single minute of latitude. This makes it effortless to measure space on nautical charts using the latitude scale on each edge of the graph.
Nautical miles additionally make it effortless to compute speed in knots.
- AIDS TO NAVIGATION
Navigational aids include many different objects used to indicate dangers in the waters and water which are safe for traveling. Both main kinds of aids to navigation comprise beacons and buoys. Beacons are fixed structures connected to the land or the seabed, and buoys are drifting objects which are anchored in position. Both buoys and beacons could be lighted or unlighted.
Navigational aids are indicated on graphs with symbols that are unique so mariners understand what every mark means and how to navigate around it. Listed below are a Couple of common symbols for aids to navigation in U.S. oceans:
Red daybeacon: Starboard side reddish day beacons are indicated with red triangles.
Green daybeacon: Portside green day beacons are indicated with squares.
Lighted markers: Lighted beacons, buoys and other markers are mentioned using a purple shadow emblem that looks like the very top of an exclamation point.
Lighthouses: Lighthouses are generally marked with a purple circle with a dot in the center.
These are just some of the countless symbols used to mark navigational aids on nautical charts. The National Oceanic and Atmospheric Administration (NOAA) provides a Complete list of symbols for aids to navigation in U.S. Chart No. 1.
U.S. Chart No. 1 also comprises conventional nautical chart symbols for submerged attributes, obstacles, anchorages, stations, prominent land features and much more. Symbols for underwater threats for example reefs, rocks and wrecks additionally indicate the thickness of this item and other critical characteristics.
Though a number of these symbols are self explanatory, taking U.S. Chart No. 1 onboard your ship lets you recognize any emblem you encounter in your nautical map.
- COMPASS ROSE
No nautical graph could be complete without a compass rose. An recognizable emblem to some experienced mariner, the compass rose comprises three concentric circles indicated with hashes and tagged with levels.
The outer circle of a compass rose points to true north, along with the internal circles point to magnetic north. If you’re using a magnetic compass for navigation, then refer to the internal bands when measuring your own bearings. I hope the article is helpful.